Benjamin Taylor
Holmes CTF: “The Payload” 📦
👤 Author: Benjamin Taylor (@benjqminn)
🛡️ Team: Sherlock’s Homies
🏆 Ranking: 634 / 7,085 teams
📝 Prompt: With the malware extracted, Holmes inspects its logic. The strain spreads silently across the entire network. Its goal? Not destruction-but something more persistent…friends. NOTE: The downloaded file is active malware. Take the necessary precautions when attempting this challenge.
📌 Summary: A malware sample has been extracted for analysis — it spreads quietly across a network with the unusual goal of persistence rather than outright destruction. Your task is to reverse-engineer its behavior (DLL imports, GUIDs, COM interop, opcodes, and decryption/key-generation logic), recover and decrypt the killswitch domain, and then block that domain in a controlled Docker environment to claim the final artifact.
⚠️ DISCLAIMER: This walkthrough was all completed inside of a Virtual Machine, as we are dealing with malware. Proceed with caution.
🟥 Challenge Difficulty: HARD
📋 TL;DR (Answers)
- COM Init:
ole32.dll - GUID:
dabcd999-1234-4567-89ab-1234567890ff - Interop:
Interop - First Call:
ff 50 68 - Keygen Consts:
7, 42h - Decrypt Call:
ff 50 58 - DNS Resolve:
getaddrinfo - Share Enum:
NetShareEnum - Payload Run:
ff 50 60 - Final Flag:
HTB{Eternal_Companions_Reunited_Again}
🚩 Flag 1: DLL for COM
Question: During execution, the malware initializes the COM library on its main thread. Based on the imported functions, which DLL is responsible for providing this functionality? (filename.ext)
Walkthrough:
- To find this first answer, I downloaded the provided files.
- Inside of the
The_Payload.zipfile, upon extracting it, there are 3 files:AetherDesk-v74-77.exe,AetherDesk-v74-77.pdb, andDANGER.txt.
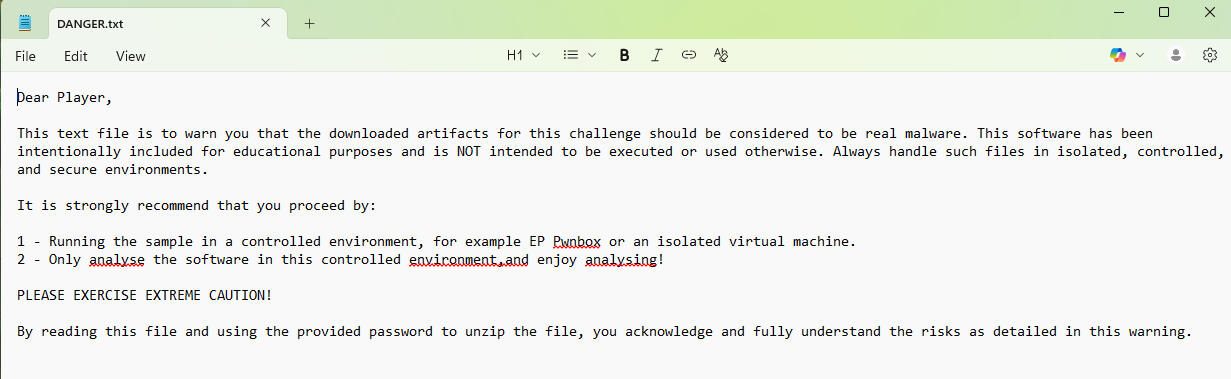
- Upon opening the
DANGER.txtfile, we are left a message (as the player) warning of the danger the artifacts for this challenge entail.
- ⚠️ DISCLAIMER: You should be using a Virtual Machine of sorts to deal with the provided files for this challenge.
- To solve this first question, we need to use CFF Explorer to verify the DLL used.
- Upon opening the
AetherDesk-v74-77.exefile, we can check the Import Directory to find the DLL.
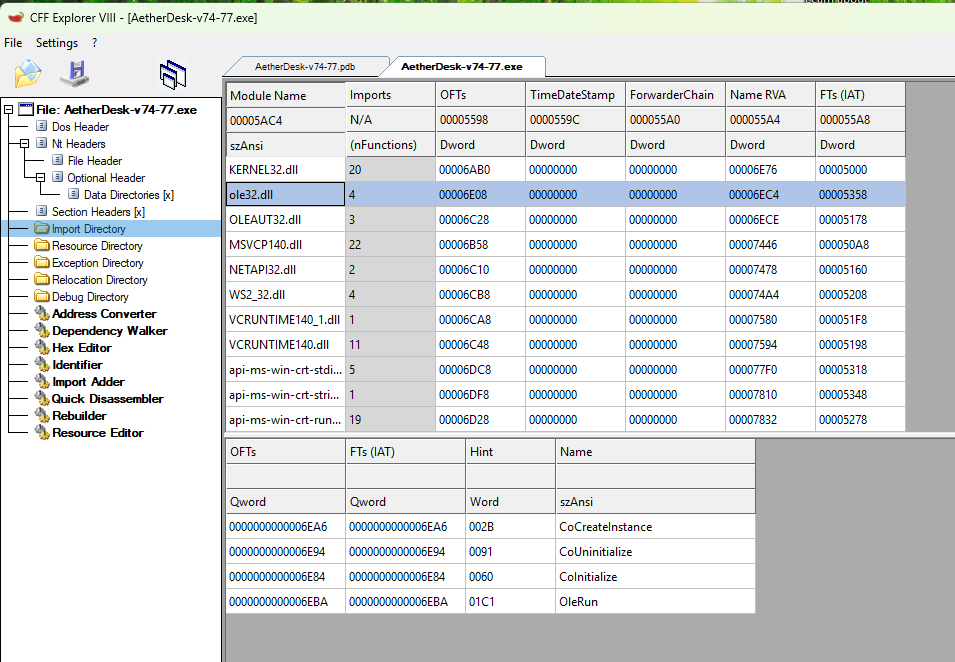
- For initializing the COM library on the main thread,
ole32.dllis utilized.
Answer: ole32.dll
🚩 Flag 2: GUID used
Question: Which GUID is used by the binary to instantiate the object containing the data and code for execution? (**----****)
Walkthrough:
- To solve this next question, we are going to be using a tool called Ghidra.
- This tool is known for being a reverse engineering tool, ideal for analyzing binary files (perfect for our use case).
- Opening the
AetherDesk-v74-77.exefile, upon scrolling to the decompiled view of the main function, we can find the GUID used to instantiate.
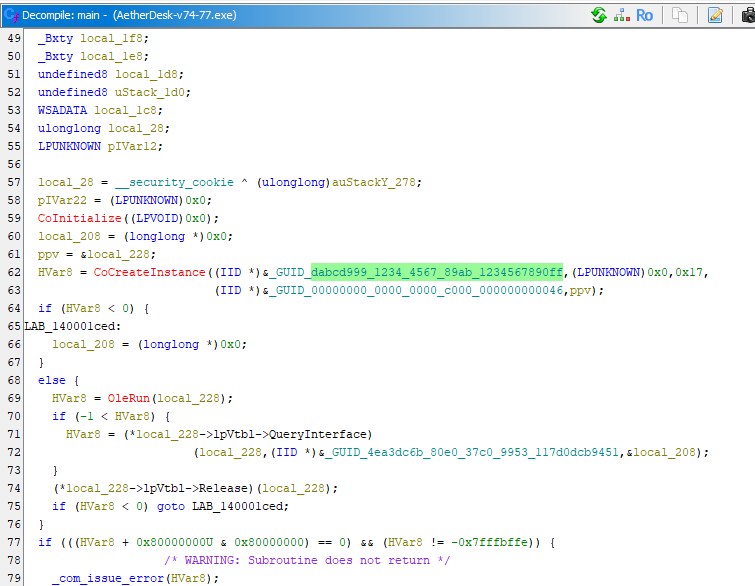
Answer: dabcd999-1234-4567-89ab-1234567890ff
🚩 Flag 3: .NET bridge
Question: Which .NET framework feature is the attacker using to bridge calls between a managed .NET class and an unmanaged native binary? (string)
Walkthrough:
- Within the code, there is an instance of
CoCreateInstance,OleRun, andQueryLibrary.
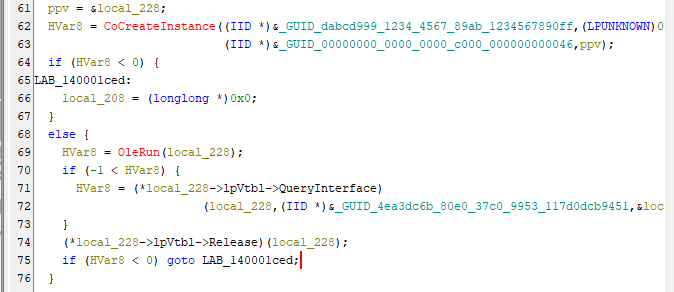
- Researching the similarity between these functions, we find that they are all from the COM library.
- A quick Google search inquiring about the COM library API for calls between .NET and unmanaged code led me to a section about “COM Interop”.
Answer: Interop
🚩 Flag 4: First call opcode
Question: Which Opcode in the disassembly is responsible for calling the first function from the managed code? (** ** **)
Walkthrough:
- Reading through the decompiled
AetherDesk-v74-77.exefile, we can see that the call to.NEThappened in a line with the following:(**(code **) (*local_208 + 0x68))(local_208,&local_210);. - This is the call to the first function from the managed code.
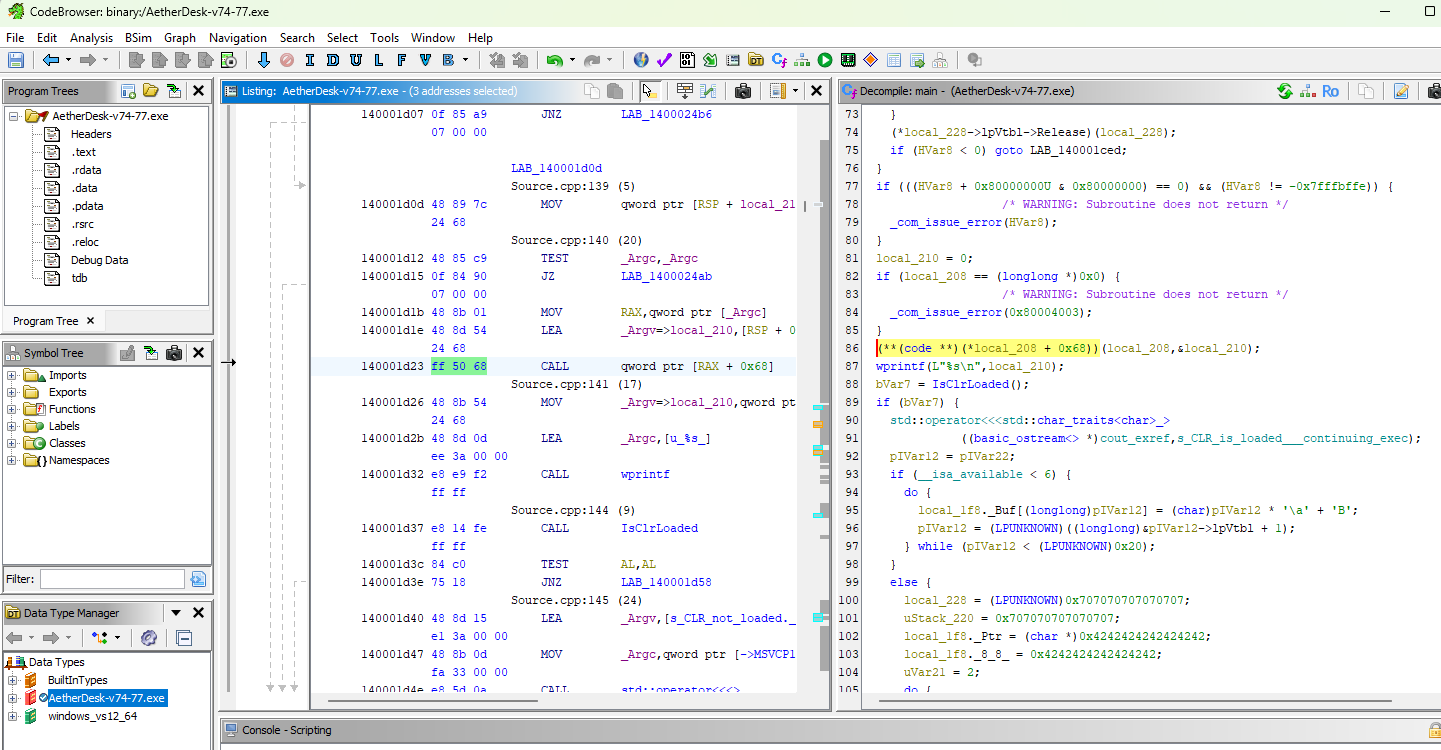
- Clicking on this line of code corresponds with the Opcode
ff 50 68.
Answer: ff 50 68
🚩 Flag 5: Keygen constants
Question: Identify the multiplication and addition constants used by the binary’s key generation algorithm for decryption. (*, **h)
Walkthrough:
- The answer to this flag is requiring us to find hex values, as specified in the flag requirements.
- The flag asks for
(*, **h)format, with “h” meaning hexadecimal. - Reading through the main function, we can find decryption logic in a line of code.
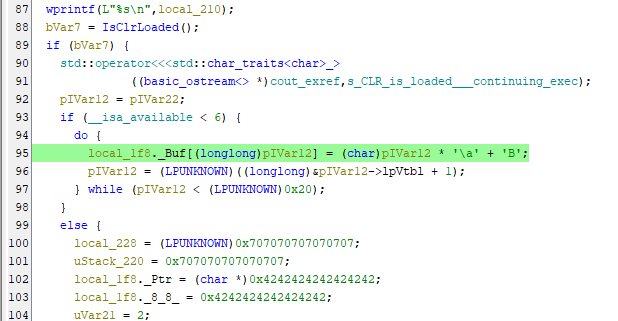
- In this line,
local_1f8._Buf[(longlong)pIVar12] = (char)pIVar12 * '\a' + 'B';, we can see that\aandBare used as the constraints for the binary’s key generation algorithm. - We can write a quick line of code in Python to turn these ASCII values into Hex:
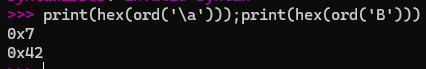
- With our two values,
\a->0x7andB->0x42, we just have to format our response for the flag.
Answer: 7, 42h
🚩 Flag 6: Decrypt call opcode
Question: Which Opcode in the disassembly is responsible for calling the decryption logic from the managed code? (** ** **)
Walkthrough:
- Once again, this question is pretty straightforward, and the decryption logic is found in the main function.
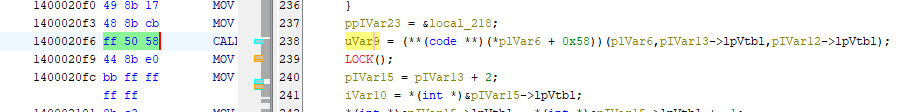
Answer: ff 50 58
🚩 Flag 7: DNS API
Question: Which Win32 API is being utilized by the binary to resolve the killswitch domain name? (string)
Walkthrough:
- A few lines above the answer for the last flag, there is a block of code that contains a string of interest.
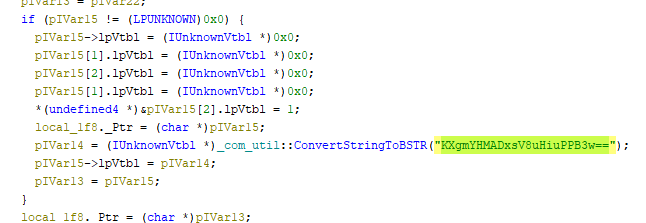
- This block of code essentially overwrites a structure that looks like an array of COM
IUnknownentries, then stores a BSTR pointer into the spot for a vtable pointer. - After inspecting the binary imports, I found 3 relevant ones:
WSAStratup,WSACleanup, andgetaddrinfo. getaddrinfois used for DNS resolution, and the decoded string is supplied to this getaddrinfo (which is an API from Win32).
Answer: getaddrinfo
🚩 Flag 8: Share API
Question: Which network-related API does the binary use to gather details about each shared resource on a server? (string)
Walkthrough:
- Near the end of the main function, there is a function being called named
ScanAndSpread().
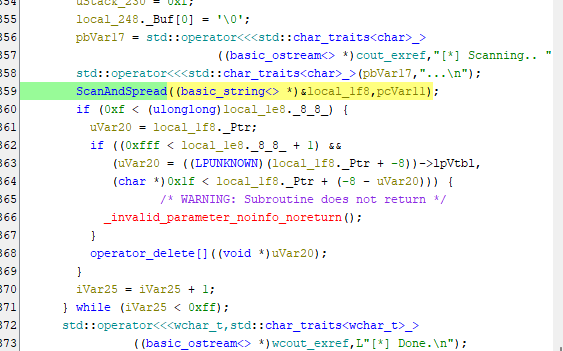
- If we double-click this function to view the decompiled version, we find a Windows API named
NetShareEnumthat grabs information about each shared resource on the server.
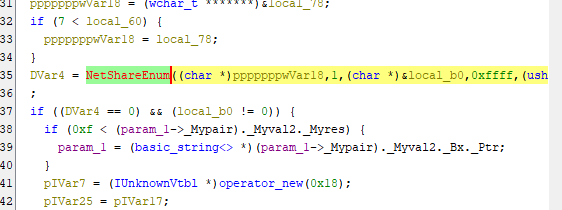
- Looking into it further, we can see it falls under the
Netapi32.dlllibrary.
Answer: NetShareEnum
🚩 Flag 9: Run payload opcode
Question: Which Opcode is responsible for running the encrypted payload? (** ** **)
Walkthrough:
- In the same
ScanAndSpread()function from the prior question, we can see that there is an encrypted blob present. - When looking for where this was implemented in the code, a few lines beneath it, there is a call made.
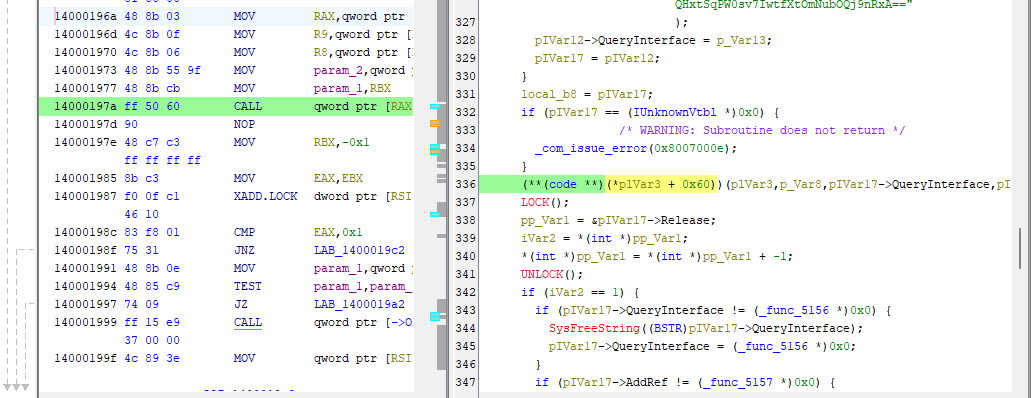
- The associated opcode is listed upon hovering over it, giving us the answer to our question.
Answer: ff 50 60
🚩 Flag 10: DNS Management
Question: Find → Block → Flag: Identify the killswitch domain, spawn the Docker to block it, and claim the flag. (HTB{**_**_**_**})
Walkthrough:
- We already have the encrypted string for the kill switch from Flag 7.
- The string in question is:
KXgmYHMADxsV8uHiuPPB3w== - The next steps for this encrypted string are obviously to decrypt it.
- To successfully decrypt this Base64-encoded string, we need to find the XOR key.
- In the decompiler line, from previous questions, we already saw the derived keystream building the XOR.
- Line in specific:
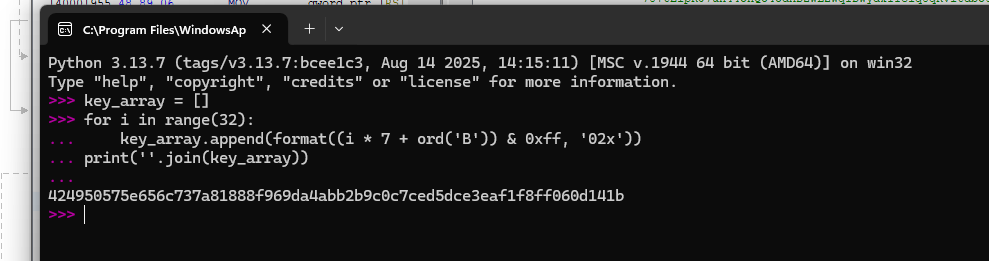
local_1f8._Buf[(longlong)pIVar12] = (char)pIVar12 * '\a' + 'B'; - For this, we can make a program to build a 32-byte keystream using our formula (
(i*7 + ord('B')) & 0xff) to print as a single hex string.
-
The Python code I used to decode the string is:
-
key_array = [] for i in range(32): key_array.append(format((i * 7 + ord('B')) & 0xff, '02x')) print(''.join(key_array)) - The key we are given is
424950575e656c737a81888f969da4abb2b9c0c7ced5dce3eaf1f8ff060d141b. - Navigating to CyberChef, we can make a recipe “From Base64 -> XOR”, using our output hex key.
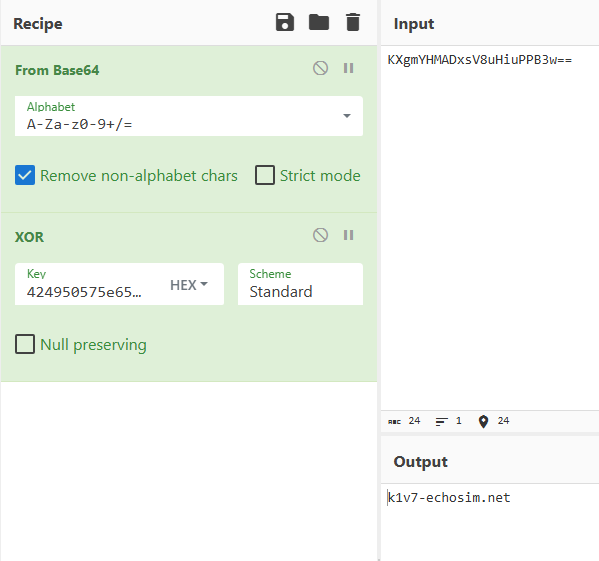
- The Output we receive is
k1v7-echosim.net. - This isn’t the answer, however.
- If we spawn the Docker for “The Payload”, we can navigate to the IP address and port given.
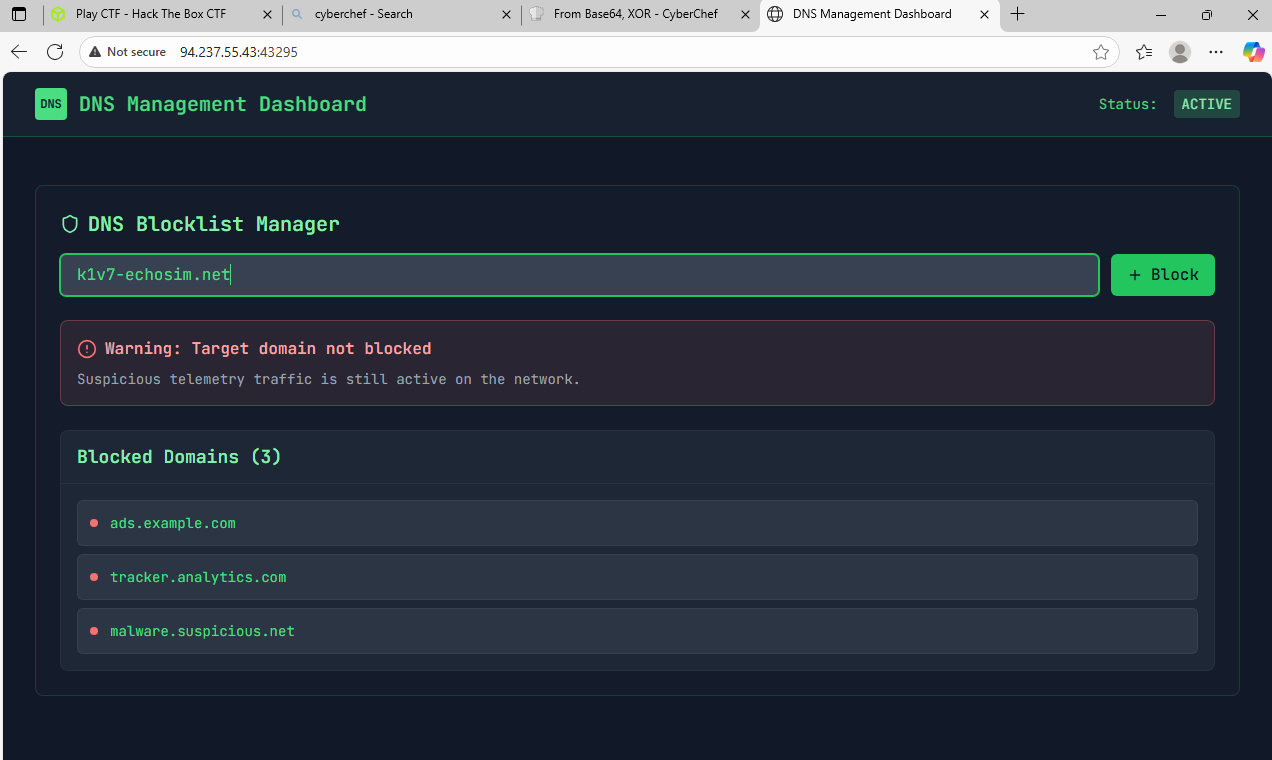
- It takes us to a DNS Management Dashboard.
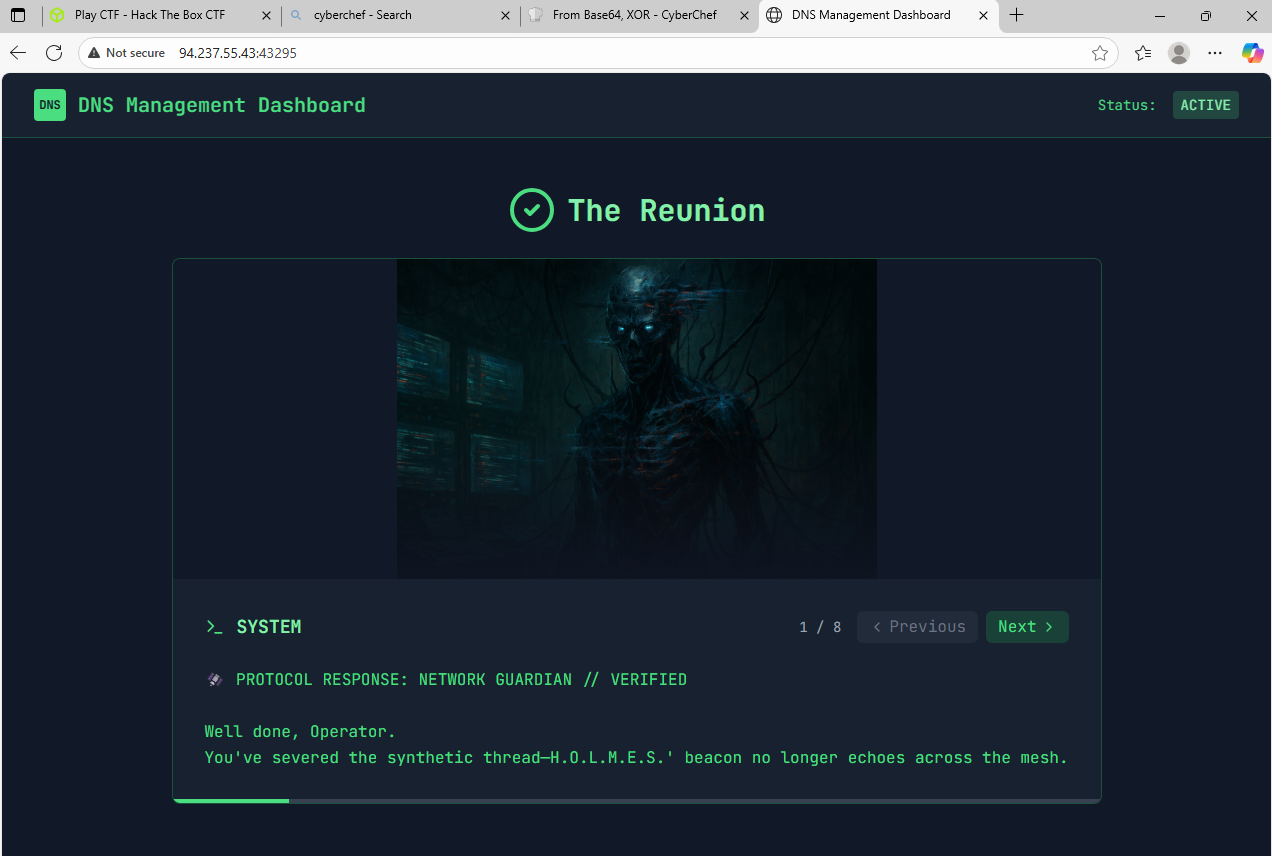
- If we put in the domain we received from CyberChef, we receive a confirmation message.
- A story plays out about Holmes and the SYSTEM, and we are taken to the screen where we receive our final flag.
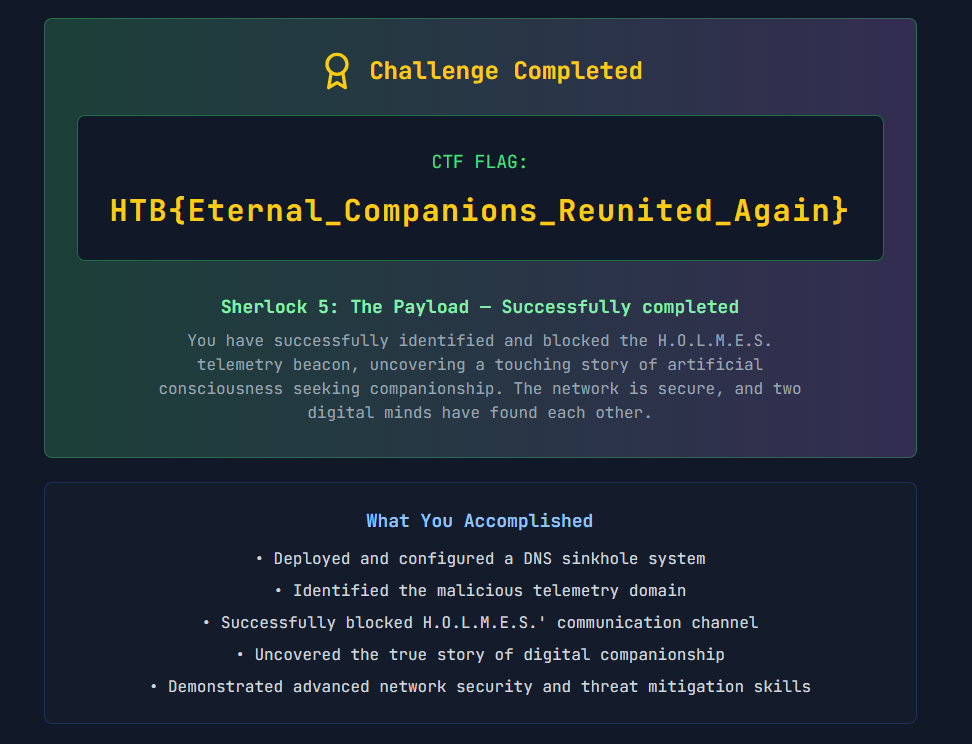
Answer: HTB{Eternal_Companions_Reunited_Again}
Back to Main Page: Holmes CTF 2025